Announcing Invariant 2.0
We’re pleased to announce the release of Invariant 2.0. This is a major update to the Invariant application, delivering on our vision of transforming how network teams validate and monitor networks.
Introducing Instant Rule Evaluation
Starting in Invariant 2.0, users can run instant connectivity checks from the UI using the Quick Trace feature.
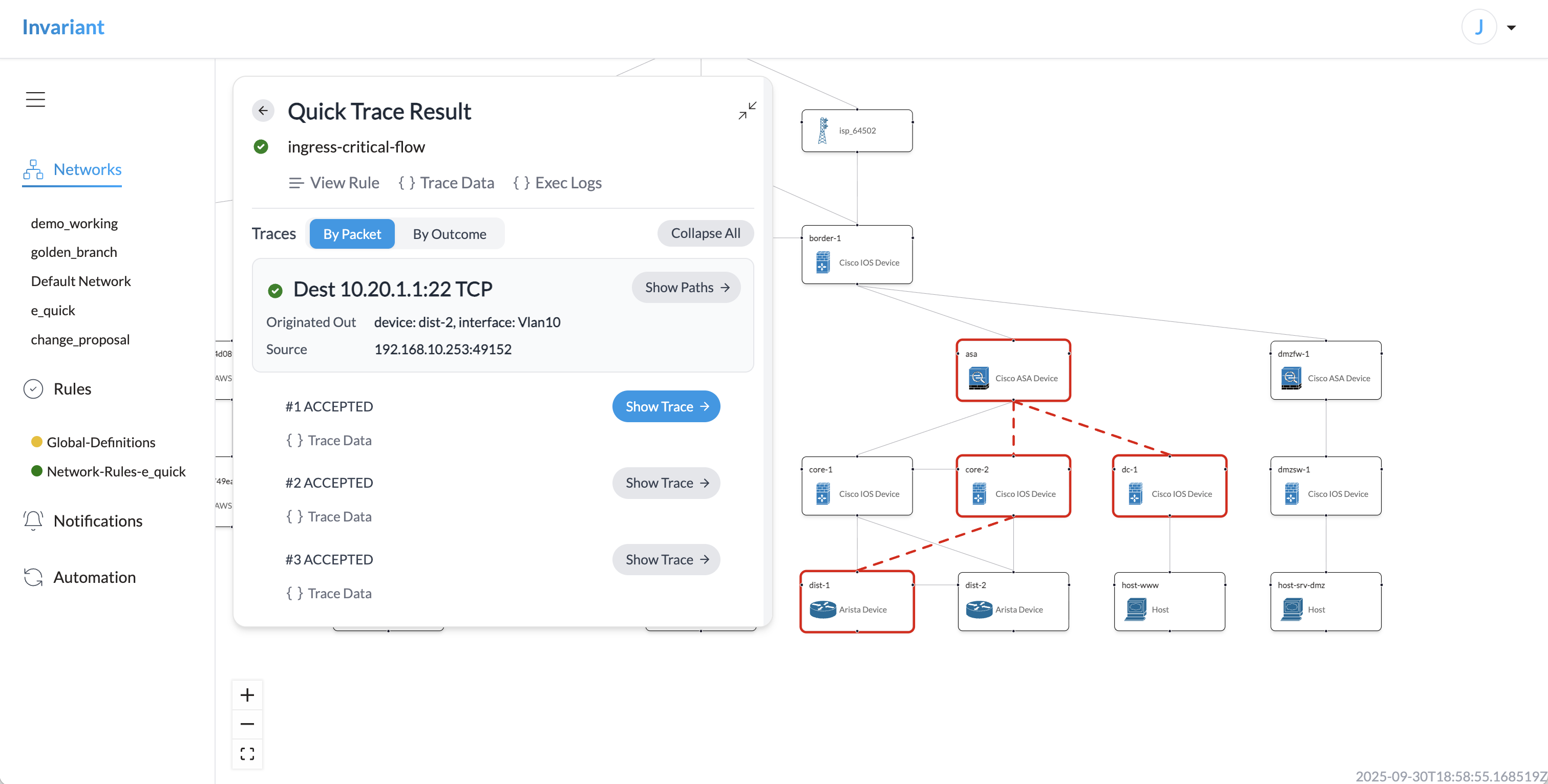
Specify protocols, a destination IP address (or CIDR), and optionally service or port constraints to exhaustively search for any connectivity issues within that range. The UI includes an interactive results viewer to visualize or view raw trace data by outcome, by source packet, or by a specific trace path.
If your team is using Aerleon, you can import your Aerleon network and service definitions into Invariant and use them in Quick Trace. You can even import a global set of definitions and overlay site-specific adjustments (e.g., site-specific CIDRs for GUEST_VLAN).
Share your instant connectivity check results with any authorized user via URL.
Target any network snapshot, including past states of the network or proposed network states.
As always, the vendor-agnostic network model considers ACLs, IPSec, BGP, OSPF, and packet transformations when performing synthetic connectivity checks.
Introducing Network Rules
Invariant 2.0 disentangles the management of network validation rules from snapshot creation. Now, authorized users can directly create, edit, and test network validation rules directly through the web.
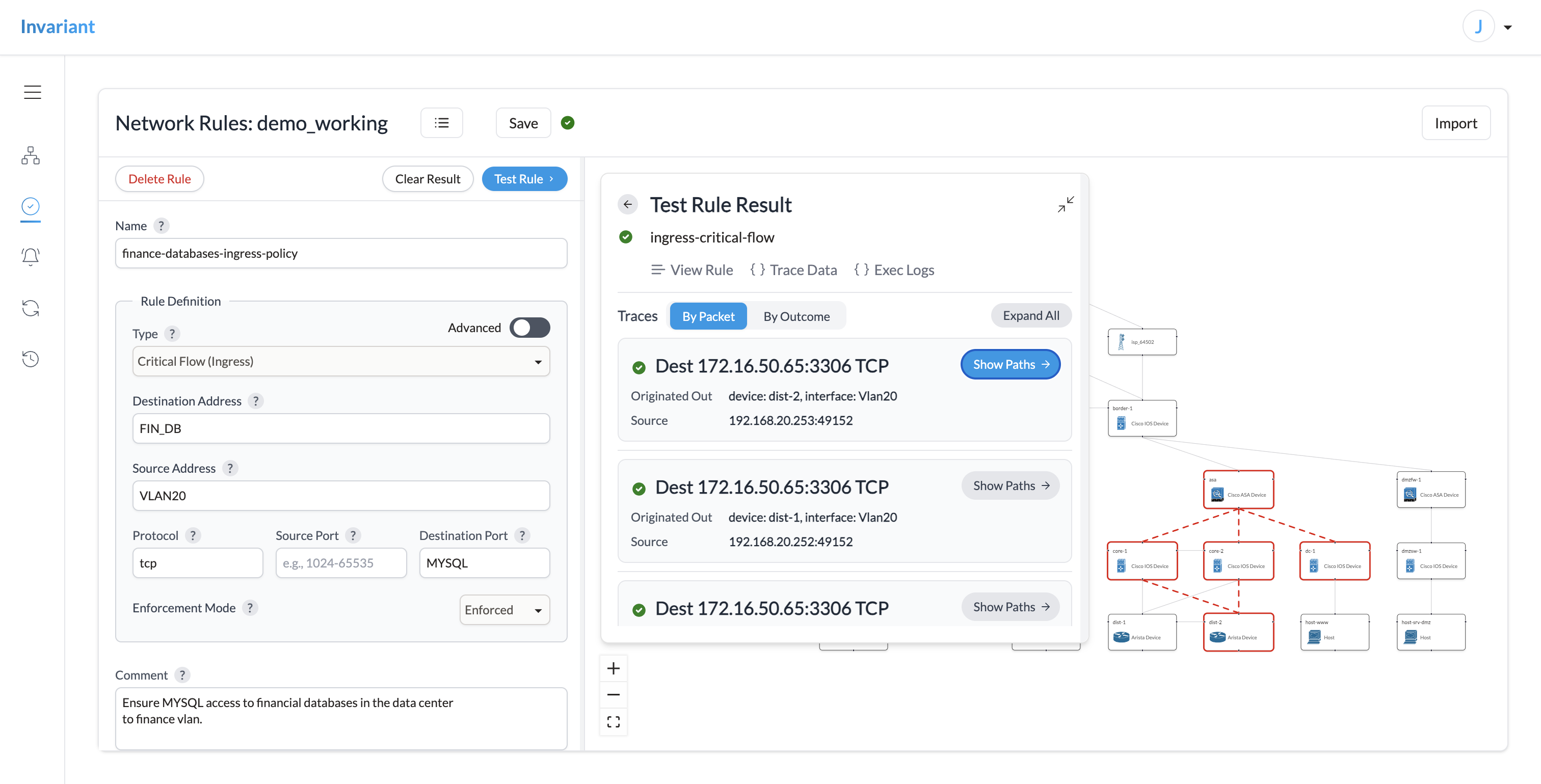
Network Rules delivers on the continuous synthetic network validation story: define your network validation rules once, and Invariant will validate every new snapshot against it. If configured, Invariant can notify your team or connected systems via Slack or email. You will get an immediate compliance verdict spanning your whole suite of connectivity and access control rules.
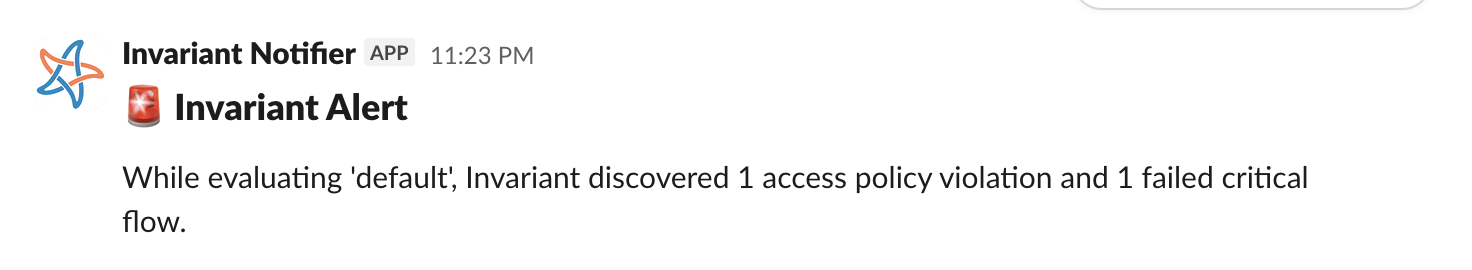
Slack Notifications
In addition to email notifications, Invariant can now be configured to post in Slack when a new snapshot fails its validation rule suite.
Democratize Access To Data
Invariant 2.0 adds the Data screen, a powerful surface for inspecting deep details of the synthetic network model across a wide range of network features.
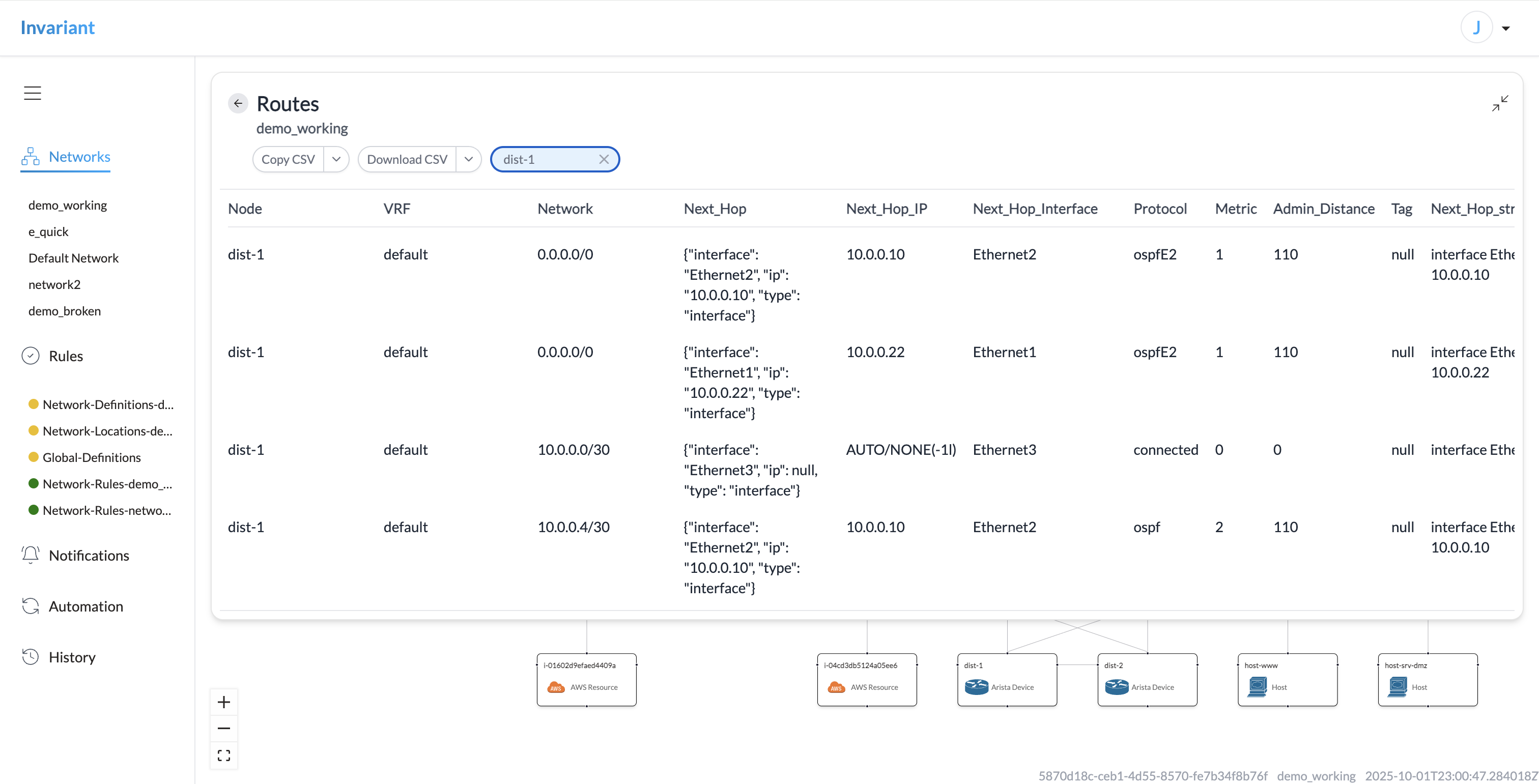
The data tables can be filtered, downloaded, and shared to authorized users via URL.
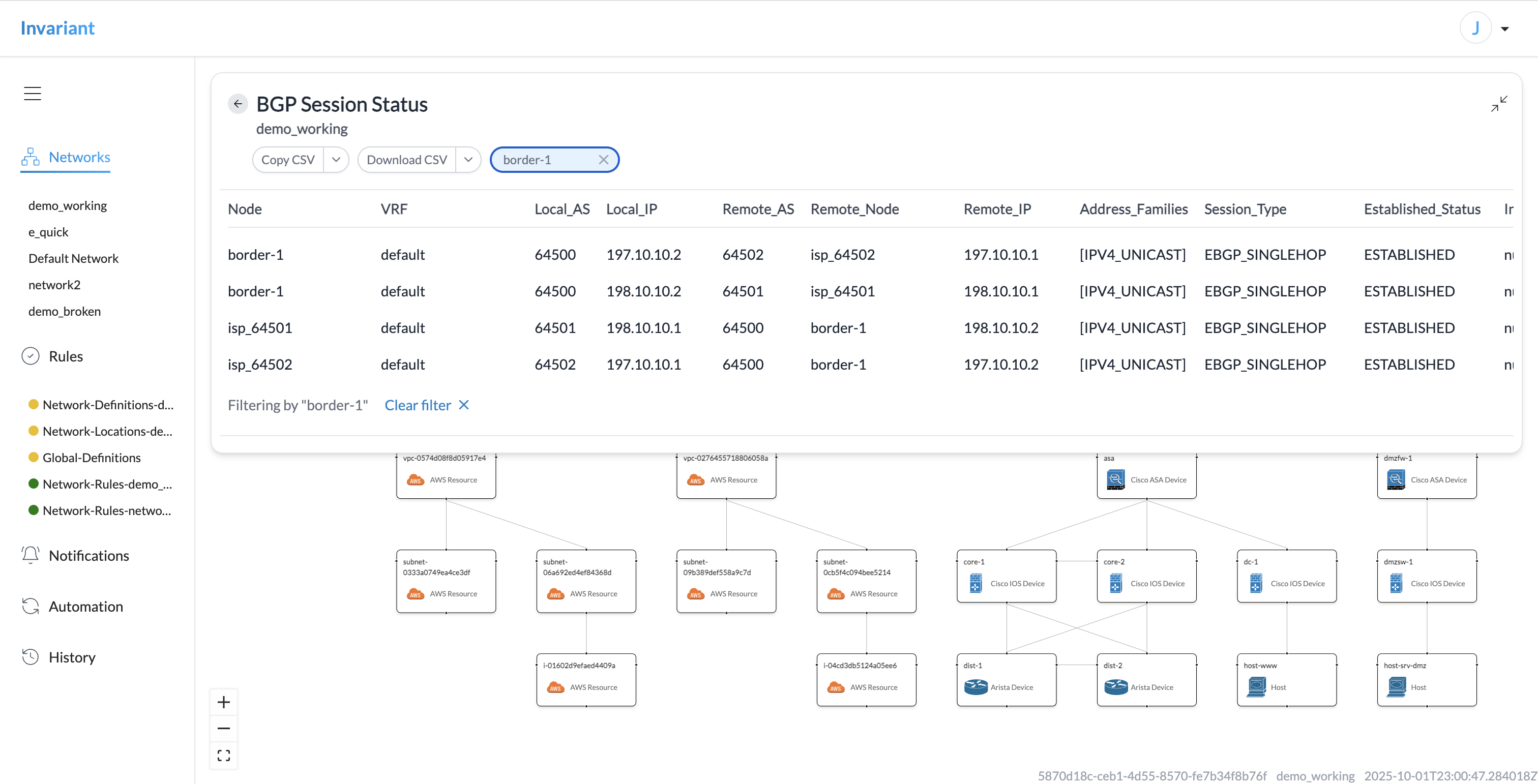
Surfacing this information allows network stakeholders to understand how core protocols are functioning (or are expected to function after proposed changes are rolled out) and troubleshoot issues when they arise. Incident response teams can instantly access deep details like estimated device route tables directly in Invariant.
Secret Mangling By Default
Starting in version 2.0, the Invariant Client will automatically mangle secrets found in network configs.
Ingestion Pipeline
The new invariant sync command, integrated into the Invariant Client, can directly fetch network configs per your fetcher.yaml config file and sync them with Invariant. For more advanced workflows, invariant fetch fetches the configs to local disk, where you can later use invariant run to create a snapshot.
Advanced Connectivity And Vulnerability Scanning Platform
The new invariant eval command, which performs instant rule evaluation against a target network snapshot, is the dark horse of this release. While the primary purpose of this command is to allow you to rapidly iterate on rules using an editor or IDE, it can also be used to deploy advanced connectivity and vulnerability scans against multiple snapshots.
Suppose you wish to investigate your network's exposure to a novel vulnerability. Write a rule that tests whether the relevant service is exposed. Evaluate this rule against the current snapshot for each network using invariant eval and receive an answer in seconds. Want to automate this function? The Invariant REST API exposes the same eval capability.
Suppose you are investigating a connectivity issue and you want to determine when the issue was first introduced. Your existing network rule suite didn't cover this particular flow. While in the UI you can quickly check the connectivity one snapshot at a time, you can apply eval --condense in a loop against all snapshots for the current network, working backward in time until the command output changes from FAIL to PASS.
General Improvements
This release includes a wide range of small improvements to ease the experience of using the system. Some highlights:
- Network snapshots may be deleted or moved between networks, and networks can be renamed or deleted.
- New unfiltered reports were introduced for simplified access to rule evaluation results:
policy_summary_all,policy_details_all, andpolicy_logs_all. - Syntax errors and other file- or policy-level issues are now surfaced more consistently in the UI and rule evaluation result data files. The UI includes a dedicated visualizer for the errors file, and position and provenance metadata are now attached to all rule evaluation results.
- The Invariant Client's interactive login feature now stores credentials in your encrypted OS keychain when available. XDG is used as a fallback.
- De-permissioned sync-only service accounts can now be created via RBAC.

